RFeye Guard – Technical Surveillance Counter Measures
RFeye Guard is a continuous TSCM (Technical Surveillance Countermeasures) solution that combines highly sensitive and broad bandwidth receivers with simple autonomous software to ensure you never miss an illicit signal.
Send Enquiry for RFeye Guard – Technical Surveillance Counter Measures
What is continuous TSCM?
In order to fully protect your facilities from the threat of illicit surveillance devices, a persistent in-place monitoring system is essential. Traditional TSCM strategies, such as bug sweeping, may be able to locate an unauthorized RF transmission at the time of the sweep. However, what if the bug is placed after the sweep has taken place? What if the bug only transmits for a few seconds in the middle of the night? What if the bug is frequency hopping, or the signal is “hidden” close to another high-power signal? A traditional bug sweep may not be able to locate these unauthorized transmissions, leaving you exposed to potential security breaches.
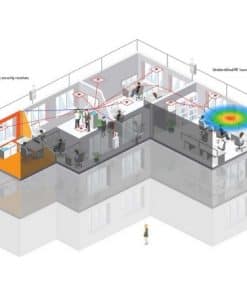
The RFeye Guard continuous TSCM system relies on a network of permanently installed, but discreet, RF receivers (RFeye Nodes) that are continuously scanning and sweeping the RF spectrum for unauthorized transmissions. If an illicit signal is detected, the location of the signal is calculated using Power On Arrival (POA) and an alert raised. This can then be displayed on the RFeye Guard software in order for further investigation work to be carried out

Automated and configurable
Monitoring the RF spectrum in a secure facility can be a challenging task. What’s normal? What’s abnormal? What frequencies should be monitored? When should things be monitored? RFeye Guard lets you create custom configurations that apply to your specific environment. It allows you to not only detect signals but be able to differentiate between friendly and potential hostile transmissions, thereby reducing false positives. You can create a whitelist for known transmitters that can also be contrasted against normal working hours. So, if a signal that looks “normal” suddenly appears outside of working hours, you’ll know about it.
By adding in automation to the operation you can enable a non-RF or non-TSCM expert to monitor the system. Sweeps and scans can be scheduled, and alerts automatically triggered. RFeye Guard ensures 24-hour, 365 day security and most importantly, peace of mind.
Flexible deployment
The modular nature of RFeye Guard means that you can choose to monitor a single room, a floor, a building or an entire campus. It is also possible to use RFeye Guard in a temporary deployment, for example TEMPEST testing, single room SCIF (Sensitive Compartmented Information Facility) monitoring, or mobile monitoring.
Via the Mission Manager API you can integrate with third party technologies to demodulate or decrypt signals e.g. Wi-Fi or cellular. This information can then be made available to Mission Manager and displayed within the interface.
DOWNLOAD DATASHEETRFEYE GUARD WORKFLOW
1) Set up
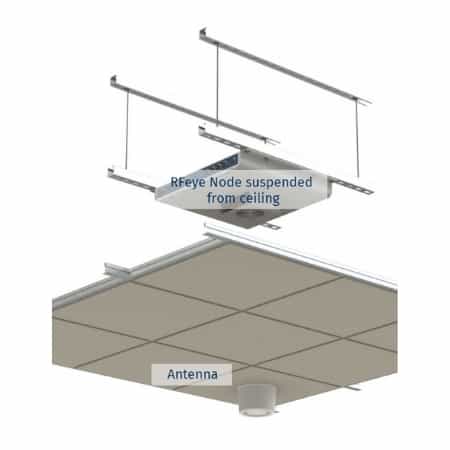
A network of RFeye Receiver Nodes are discreetly installed inside the building to be protected. They are typically mounted in the ceiling using the ceiling mounting kit. Often a separate RFeye Node is mounted externally to differentiate between signals originating inside or outside of the building. To ensure accuracy all Nodes need to be synchronized to the same time. Normally this would done using GPS, but inside a building GPS is not universally available. To solve this issue the Guard system uses the RFeye SyncLinc system to ensure exceptional timing accuracy.
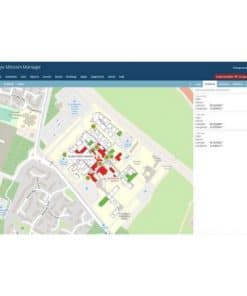
A plan of the floor or building to be monitored can be uploaded to the system and the position of the Nodes mapped out. This plan will then be able to show the geo location of any signals when they are found.

2) Initial survey
The RFeye Nodes are controlled and managed by the RFeye Mission and RFeye Site software packages. Once initial Node installation is complete a site survey is performed to determine what “normal” looks like. The system sweeps the specified frequency range and records all signals detected. The analyst can then go back through the data and perform geolocations to identify the signals that are allowed and add them to a “whitelist” and add any suspect signals to a blacklist. This whitelist/blacklist can specify when a signal should be allowed to broadcast. For example, cell phone transmissions may be allowed during business hours but not at 2am.
This survey phase can also act as a test of an organization’s Operational Security (OPSEC) policies. OPSEC may state that no devices are allowed in a building at any time. The RFeye Guard survey will be able to quickly see if that policy is being adhered to.
3) Persistent monitoring
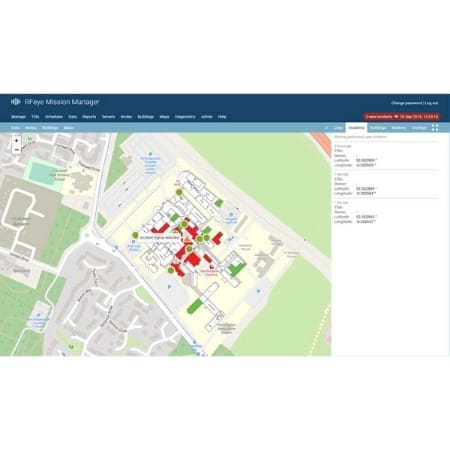
When the survey is complete and the result analyzed, RFeye Guard can then be switched to continuous monitoring mode. It will then look for any suspect signals not on the whitelist and automatically alert security to the presence of an unauthorized device.

4) Actions on
When a suspect signal is detected, there are a number of options open to the security team:
1 – Seek and destroy
Using the geolocation data from RFeye Guard, the team could search out the device, remove it from the area and destroy it. However, there may be times when the team would want to leave the device in place.
2 – Denial and deception
Once a surveillance device is known to exist it can be used against the adversary to purposely feed them misinformation or gather evidence for later prosecutions. RFeye Guard can help the team build up a historic picture of the device in post analysis.

5) Post analysis
Any signal detected is stored within the RFeye Guard database. This data can be historically extracted and used to determine the capabilities of the device, its location (does it move over time?), its modulation and operating times. The information could be used for countermeasure development, evidence collection or in the denial and deception phase.